2. Firewall Ruleset Review
Firewall ruleset review provides Network Engineers, Network Security, and Compliance Analysts with functionality for:
- Easy review of firewall access rules and object groups using the Access Rules and Object Groups reports.
- Automatic identification of configuration risks using the Risks and Warnings report.
- Validating recent policy modifications as part of a configuration change review process using the Change Tracking report.
How to Review Access Rules
An independent review of firewall policies has to be periodically conducted to ensure that network access rules are correctly implemented and documented. It is important because lack of access rule review leads to unexpected network access vulnerabilities.
- Frequency: each time firewall policies are changed, and at least once a quarter
- How to do it:
- Step 1: given a workspace populated with network device configurations, open the Access Rule table from the main menu (top left)
- Step 2: leverage the “Column Search” feature or the “Compare” feature to show the rules in scope of your verification
- For instance, filter the “Device” column to only show rules for a specific device, or filter the “Binding (ACL)” column to only show rules bound to a specific interface, or use the “Compare” feature to only show rules added or removed recently
- Step 3: review values for the source, destination, service, binding, risk, and description of each rule in scope
- The “Description” column captures comment, description, or justification from the device configuration
- The “Risk” and “Risk Criticality” columns are populated by NP-View during the automated risk analysis
- Step 4: to identify rules that are not justified, sort the table by “Description”. Empty values will be shown at the bottom.
- Step 5: to document your review process, double click on the “Comment” or “Comment Status” cells to add your own comment. The comment status can be either “Verified” or “To Review” or “To Revise”
- Step 6: to save an evidence of your review process, export the table to Excel using the export options in the top right corner of the table
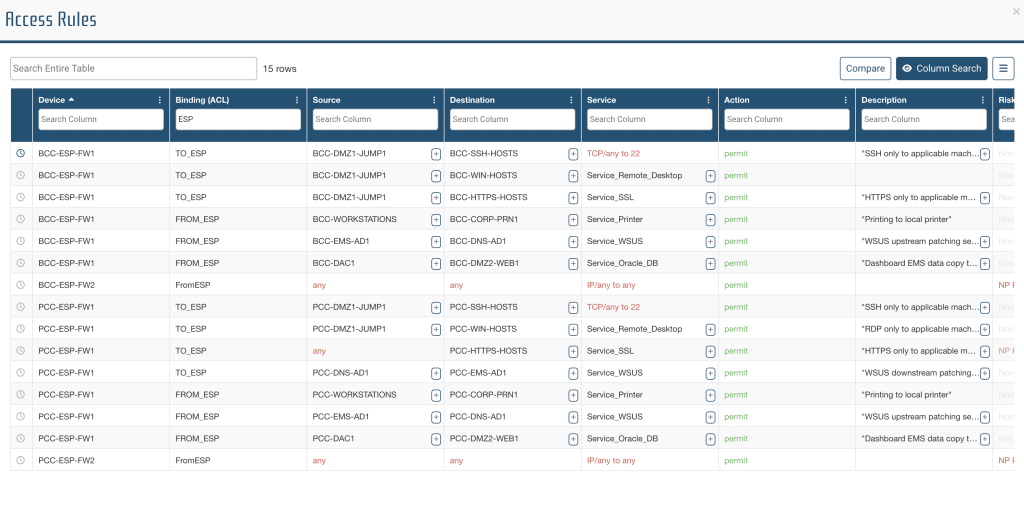
Access Rules Table
The Access Rules report provides the users with complete details on each Access Rule with the ability to add justifications and actions.
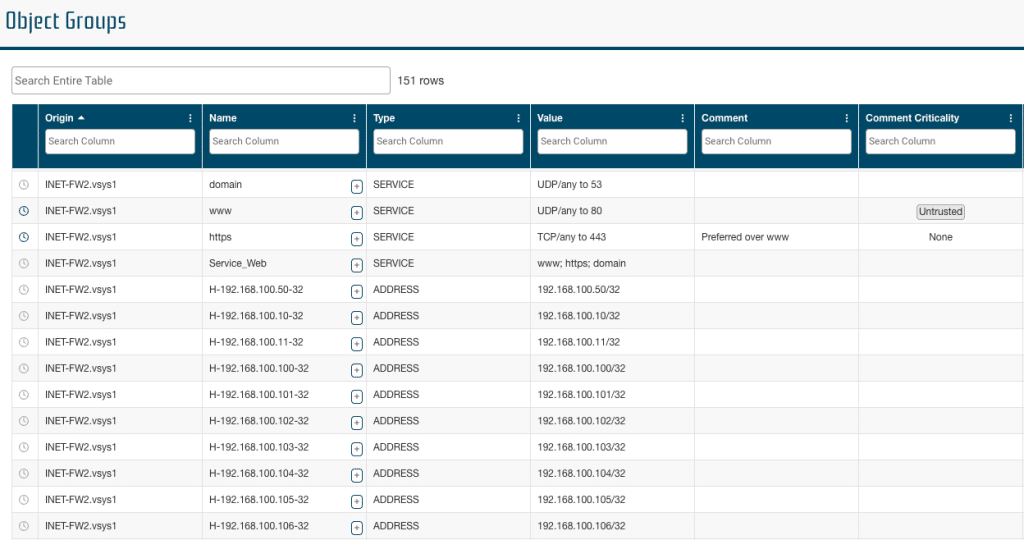
Object Groups
The Object Groups report provides the users with complete details on each Object Group with the ability to add justifications and actions.
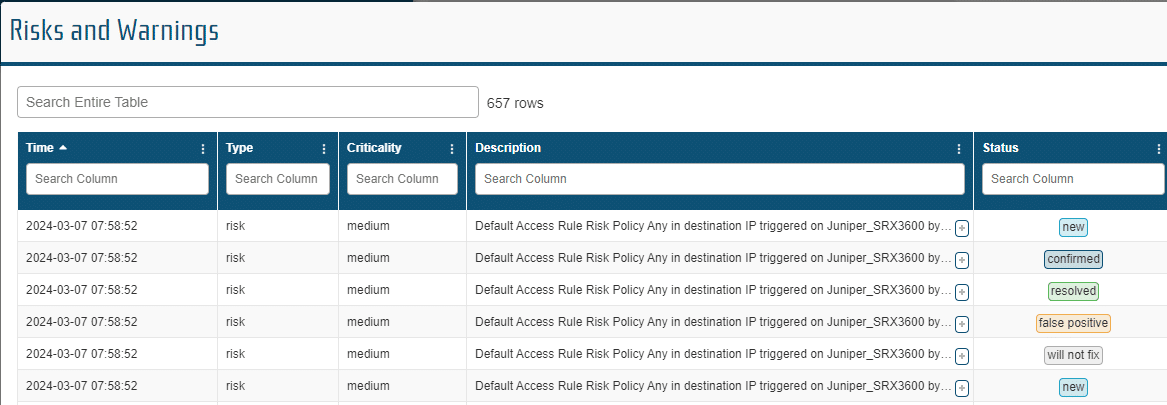
Risks and Warnings
As modifications are made to the network, the Network Perception default Policies and Requirements identify potential risks. The Risks and Warnings report provides the users with a summary of the potential risks and their criticality with the ability to add actions and comments.
Change Tracking
As modifications are made to the network and the updated configuration files are imported, the changes are logged in the Change Tracking table.