3. Segmentation Verification
Segmentation verification provides the Networking Team and Audit Team with capabilities that allows users to:
- Assess correctness of network segmentation
- Identify risky network connectivity paths
- Understand exposure of vulnerable assets
Network Segmentation Accuracy
NP-View be used to verify the accuracy of your network segmentation.
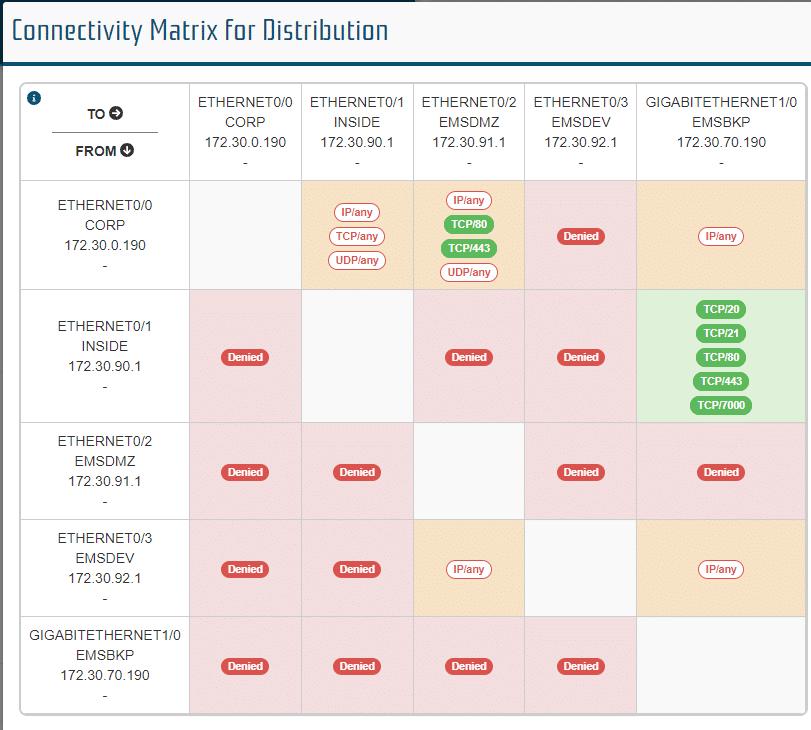
The connectivity matrix which is available from the device info panel can be used to verify open ports between devices.
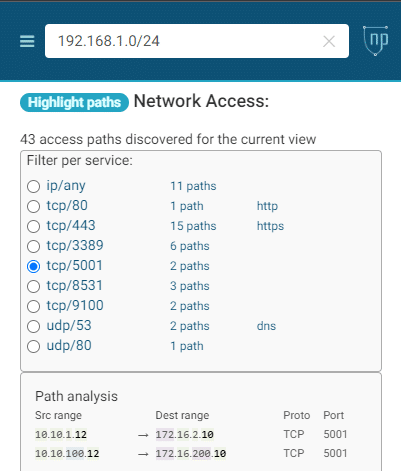
Inbound and outbound connections can be verified for each network using the highlight paths function.
Identifying Risky Connectivity Paths
Using industry best practices, Network Perception automatically identifies potential risks related to network configurations. Using the Network Perception Connectivity Path analysis, the user can review each of the highlighted risks and make a judgment on action.
Exposure of Vulnerable Assets – Vulnerability Analytics
NP-View provides your security team with a single pane of glass for reviewing network vulnerability exposure. With the addition of scanner data or data from a vulnerability data service, vulnerabilities can be tracked across your network.
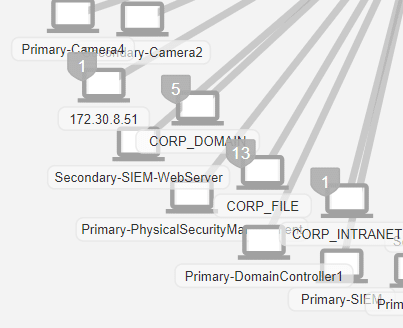
Topology Display of Vulnerabilities
When scanned data has been added to a workspace, and a topology view is built that also includes that scan data, nodes on the topology of that view will be marked with a shield indicating the presence of vulnerabilities.
These shields can be toggled on and off using the topology settings menu.
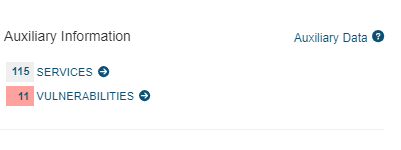
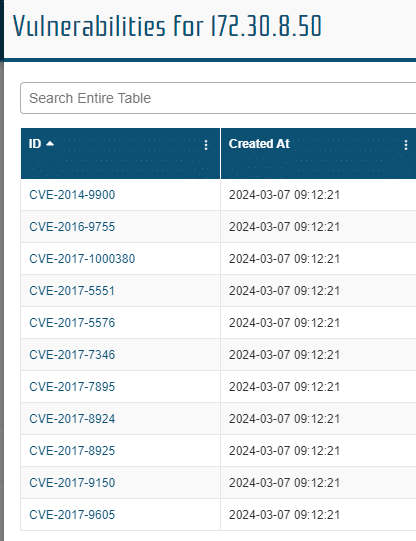
Device Panel Display of Vulnerabilities
Firewalls, Gateways, and Hosts may contain vulnerability and service information imported from scans. Clicking on any of these nodes in a View that contains vulnerability information, will display it in the info panel that opens over the main menu.
Clicking on the Vulnerabilities link will present a pop out with the vulnerability details.