
Network Security Auditing Software
NP-View’s leading platform includes a collection of cyber risk alerts designed through collaboration with industry experts to ensure that misconfigurations and network vulnerabilities are instantly identified.
NP-View’s Solutions to Network Security Auditing
Proactive Risk Alerts
Receive and review risk alerts for overly permissive rules, unsecured network protocols, firewall misconfigurations, and more.
Network Access Vulnerability Identification
With NP-View’s path analysis, know which paths an asset can take through the network to assess your attack surface.
Management of Change
Each time a change in the network is detected, NP-View automatically runs a comprehensive analysis of the modified configuration files to report any issues.
Rapid Security Assessments
Generate comprehensive security assessment reports with NP-View for all supported devices. Exportable in human and machine-readable formats.
NP-View Path Analysis Demo
“The great thing about NP-View Enterprise is that even though it needs to operate in the production environment, we don’t have to go in and manually pull the data because NP-View Enterprise automatically grabs the data it needs.”
— David Fletcher, Lead Cybersecurity Analyst at PSEG
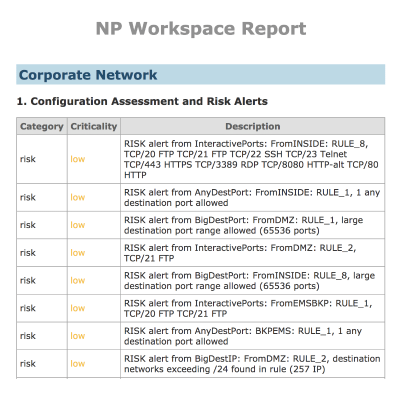
Risk Alerts
Customizable and Expandable
Risk alerts included:
- Overly permissive rules
- Unsecured network protocols
- Misconfigurations in configuration files
- Unused rules and object groups
“Back then, we would have to take the raw file and parse it manually. I simply did not have the capacity to handle the work quickly and efficiently. Thankfully, we now use NP-View.”
— Michiko Sell, NERC CIP Services Supervisor at NAES
Network Security Auditing FAQ
A network security audit is a systematic evaluation of an organization’s computer network infrastructure, systems, and practices to identify vulnerabilities, assess security risks, and ensure compliance with security policies and regulations. It involves a comprehensive review of the network’s architecture, configuration, protocols, devices, and the overall security posture.
A network security audit checklist is a comprehensive list of items or tasks that auditors can use as a guide during the network security audit process. It helps ensure that all relevant aspects of the network infrastructure and security controls are assessed and evaluated. While the specific items on a checklist may vary based on the organization’s needs, here are some common elements typically included:
- Network Inventory
- Network Architecture
- Access Controls
- Network Perimeter Security
- Network Monitoring
- Wireless Network Security
- Vulnerability Management
- Data Protection
Performing a network security audit involves several steps to thoroughly assess the network infrastructure and identify potential vulnerabilities. Here is a general overview of the process:
- Define Audit Scope and Objectives
- Gather Network Information
- Identify Assets and Vulnerabilities
- Assess Security Controls
- Review Network Architecture and Configuration
- Conduct Penetration Testing
- Assess Compliance Requirements
- Analyze Findings and Prioritize Risks
- Provide Recommendations and Remediation Steps
- Monitor and Follow-Up


