Cyber Resilience: NP-View's Proactive Approach to Safeguarding Network Infrastructure

Introduction
Recently it was reported that a major Chicago children’s hospital (Link) was forced to shutdown their network, email, and phone systems due to a cyber incident for an indefinite amount of time. Our CEO, Robin Berthier, has been asked to speak on the topic by numerous agencies regarding what may have happened, the potential impact, reasoning behind such an act, and expected recovery times. All good questions, however, one critically important question remains: What proactive measures can organizations take to safeguard against such incidents as the risk and frequency of reported incidents continue to increase exponentially?
What is Cyber Hygiene?
Cyber hygiene is the set of practices and proactive measures that organizations adopt to ensure a robust, healthy, and secure digital environment. Taking care of the basic cybersecurity essentials provides a solid return on investment in addressing cyber risk.
- Asset Inventory – Build an accurate asset list of hardware and software used an environment to understand what needs to be protected ensuring there are no blind spots left unprotected.
- Asset Baseline and Backup – Document how equipment is configured and ensure backups are performed and fully tested to ensure they will work if needed in the case of an incident.
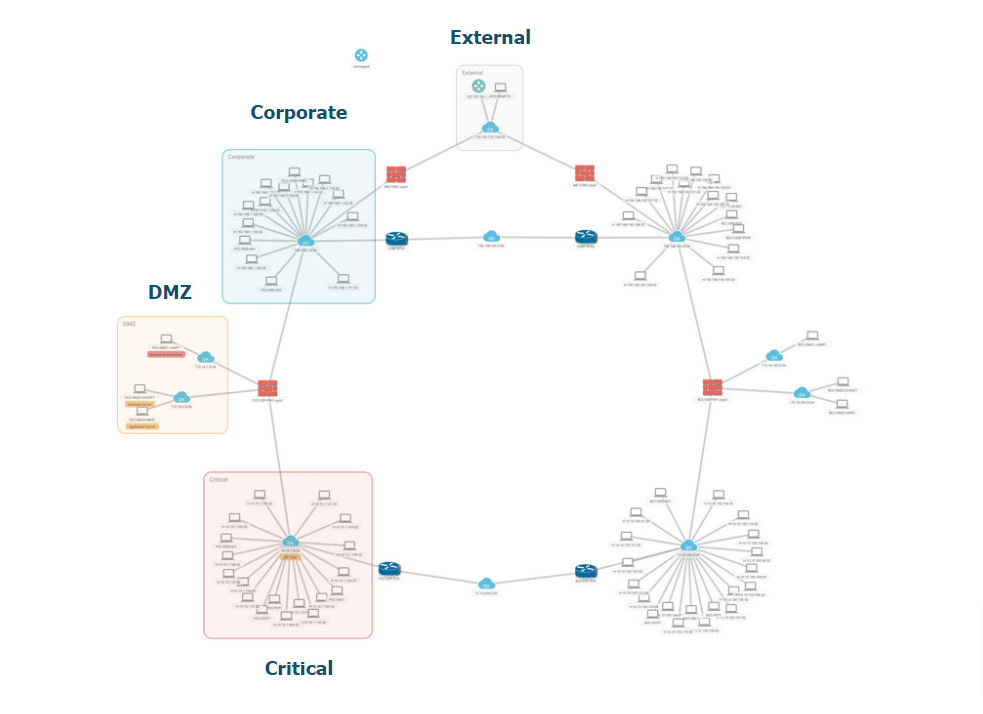
- Network Topology Map – Document how equipment is connected together which allows network defense implementation to be planned.
- Data Flow Diagrams – Document how data traverses the network and look for access paths which could bypass your segmentation policy.
- Business Continuity and Incident Response Planning – Document your plan in the case of physical or cyber incident and test it quarterly.
These fundamental steps are essential to ensure that your organization comprehensively understands its attack surface and could effectively respond to a potential incident. There are several other best practices including patch management, identity management, malicious software prevention, and cybersecurity training which are also very important as next steps but outside the scope of this post.
How Can NP-View Help?
We have been asked, “How can NP-View help?” We will detail this in a multi-part blog series on several key areas and show how this approach is part of a path to cyber resilience. We will start with a high level summary.
NP-View is a network modeling platform which provides several key features that help an organization take a proactive approach to cybersecurity and compliance in a passive, offline manner requiring no modification to the network hardware or configuration.
Network Visibility: NP-View will parse and process network equipment configuration files that were manually or systematically imported which can act as backups in the case of an incident. The platform will automatically build a comprehensive model of the network environment as a simulation. This provides full visibility of the network allowing for critical path analysis to ensure access permissions are as intended and to understand what lateral movements are possible within the network. The platform also provides an inventory of all assets within the scope of the network equipment’s configuration.
Network Segmentation: NP-View provides clear insight into the segmentation strategy configured within the network allowing you to verify that network segments are properly isolated to prevent lateral movement of threats. Once baselines are configured, the platform can alert users to configuration changes which violate policy.
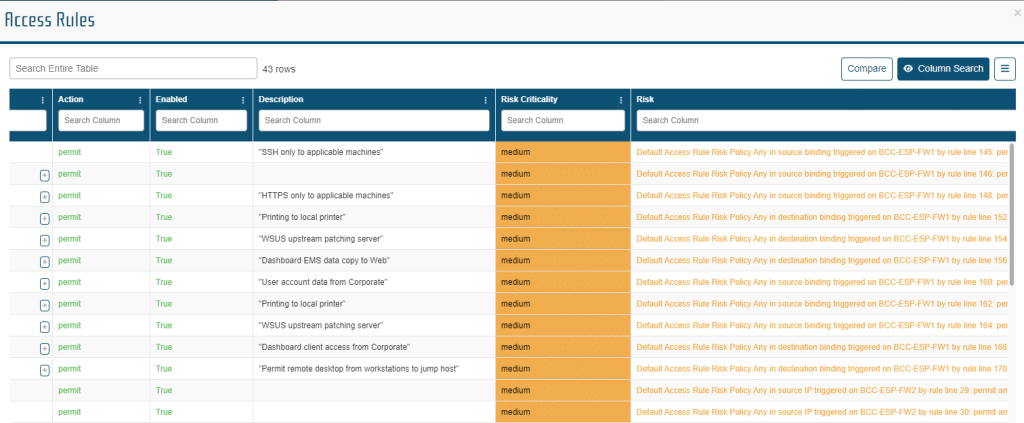
Firewall Auditing: NP-View allows the user to analyze network traffic access paths and the associated firewall rules which permit or deny access to specific networks or assets. The platform identifies high risk and overly permissive rules while allowing for documentation and justification of rule configurations.
The NP-View platform provides a proactive approach to cybersecurity which assists with good cyber hygiene as critical steps in the pursuit of cyber resilience. In future posts we will dive into each of the three areas above in more detail to show why each is a critical component to include in your cybersecurity program.
Download our Whitepaper on Cyber Hygiene here and learn how to establish a culture of cybersecurity, compliance, and resilience.
If you want more insight, please contact us at sales@network-percpeption.com