Network Segmentation Software
Reduce the manual time required to analyze network paths available, enabling faster understanding of asset exposure and simulation of all possible network connectivity paths.
NP-View’s Solutions to Network Segmentation
Topology Mapping
Visualize your network through a top-down view. NP-View’s most intuitive feature lets users arrange their network view for efficient network upkeep.
Network Vulnerability Identification
With NP-View’s path analysis, know which paths an asset can take through the network to assess your attack surface.
Management of Change
Each time a change in the network is detected, NP-View automatically runs a comprehensive analysis of the modified configuration files to report any issues.
Rapid Security Assessments
Generate comprehensive security assessment reports with NP-View for all supported devices. Exportable in human and machine-readable formats.
NP-View Topology Demo
“NP-View is exactly what we needed. Internally, we can design network diagrams, track equipment inventory, and monitor configurations from switches, routers, and firewalls.”
— Todd Chwialkowski, Senior NERC Compliance Specialist, EDF Renewables
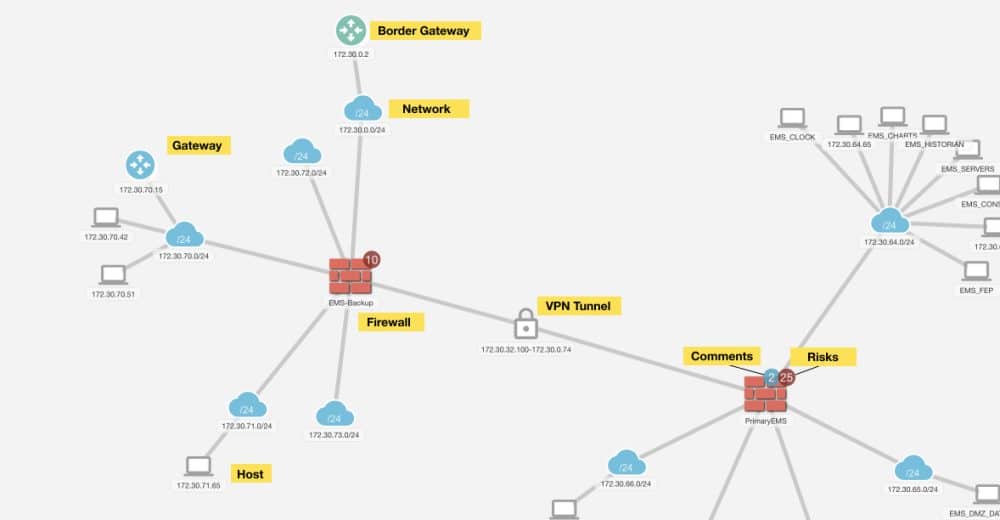
Network Topology Map
Accurate View of Your Network
- NP-View’s visualization engine will process your information and create a dynamic, interactive network diagram
- Drag & drop functionality makes it easy for users to configure their workspace to the view they want
- Risk alerts and user comments appear on the relevant device
“Back then, we would have to take the raw file and parse it manually. I simply did not have the capacity to handle the work quickly and efficiently. Thankfully, we now use NP-View.”
— Michiko Sell, NERC CIP Services Supervisor at NAES
Network Segmentation FAQ
A network risk assessment is a systematic evaluation of the potential security risks and vulnerabilities within an organization’s network infrastructure. The primary goal of a network risk assessment is to identify, analyze, and prioritize potential threats and weaknesses in the network’s architecture, protocols, devices, and software.
Here are the key components and steps typically involved in a network risk assessment:
Scope Definition: Define the scope of the assessment, including the specific network components, systems, and assets to be evaluated.
Asset Inventory: Create an inventory of all network assets, including servers, workstations, routers, switches, firewalls, and other devices.
Threat Identification: Identify potential threats and vulnerabilities that could affect the network. These threats can include malware, unauthorized access, data breaches, DDoS attacks, and more.
Vulnerability Assessment: Use tools and techniques to scan and assess the network for known vulnerabilities in hardware, software, and configurations.
Risk Analysis: Evaluate the potential impact and likelihood of each identified threat. This involves assessing the potential harm or loss that could result from an attack and the probability of that attack occurring.
Risk Prioritization: Assign risk scores to each identified threat and vulnerability to prioritize them based on their severity and potential impact on the network.
Security Controls Assessment: Evaluate the effectiveness of existing security controls, such as firewalls, intrusion detection systems, access controls, and encryption mechanisms.
Compliance Assessment: Ensure that the network complies with relevant regulatory requirements and industry standards, such as GDPR, HIPAA, or ISO 27001.
Gap Analysis: Identify gaps and weaknesses in the current security measures and policies.
Recommendations: Provide recommendations and action plans to address and mitigate identified risks. These recommendations may include software updates, configuration changes, policy improvements, and employee training.
Report Generation: Compile the findings, analysis, and recommendations into a comprehensive report for stakeholders.
Risk Mitigation: Implement the recommended security measures and continuously monitor the network for new threats and vulnerabilities.
A network risk, in the context of computer networks and information technology, refers to the potential for adverse events or situations that can compromise the confidentiality, integrity, availability, or overall security of a network and its connected systems and data. These risks can arise from various sources and can manifest in different forms, but they all have the potential to disrupt network operations or result in unauthorized access, data breaches, financial losses, or damage to an organization’s reputation.


