The “WHY” and "HOW" to become NERC CIP Compliance

The purpose of the NERC CIP standards is to ensure the reliability and security of the North American power grid by establishing cybersecurity standards that BES (Bulk Electric Systems) owners and operators must follow. NERC enforces these standards, and non-compliance can result in significant penalties and fines. Compliance with NERC CIP is mandatory for all BES owners and operators in North America.
NERC CIP compliance is important for ensuring the reliability and security of the electric grid, meeting regulatory requirements, and improving risk management practices. Compliance teams in charge of verifying network configurations are meeting the dual challenge of highly technical and dynamic environments. On the one hand, networks are becoming larger and more complex. On the other hand, organizations are continuously evolving their technology, use cases, and personnel. As a result, disruptions can impact the ability of compliance teams to ensure that their regulatory framework is properly followed.
Hear Network’s Perception’s latest perspective on the WHY and the HOW you can stay compliant, avoid fines and protect your network.
Why being Compliant is important:

1. Protect the electric grid: NERC CIP compliance helps protect the electric grid, which is essential for maintaining the reliable delivery of electricity to homes and businesses. The grid is a critical infrastructure that supports the functioning of other critical infrastructure sectors, such as healthcare, finance, and transportation. A failure or disruption of the grid could have severe consequences for public safety and the economy.
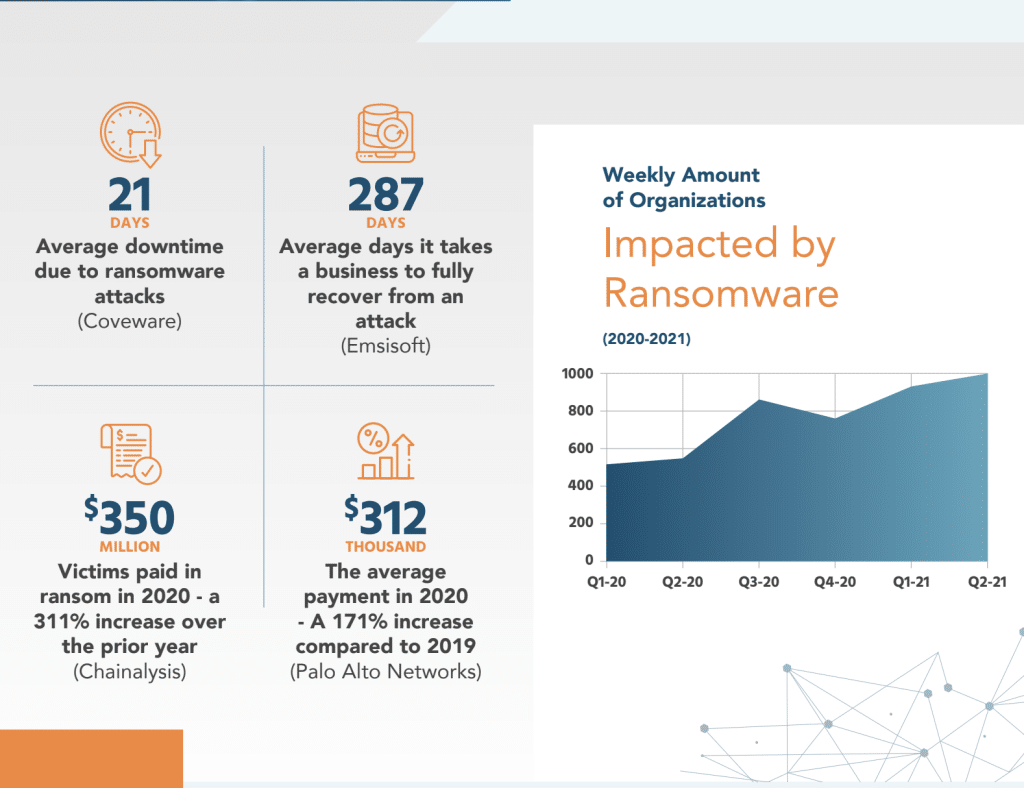
2. Ensure cyber security: NERC CIP compliance helps ensure that the electric grid is protected against cyber-attacks. Cyber-attacks on the grid can cause power outages, disrupt critical services, and compromise sensitive information. With the increase in cyber-attacks, (Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025), Compliance with NERC CIP standards helps to mitigate these risks, and fines and ensures that proper measures are in place to prevent and respond to cyber threats.
3. Meet regulatory requirements: Compliance with NERC CIP standards is a regulatory requirement for electric utilities and other entities that are responsible for the operation and maintenance of the electric grid. Non-compliance can result in significant penalties and fines, and can also damage the reputation of the organization.
4. Improve risk management: NERC CIP compliance requires organizations to identify and assess potential risks to the electric grid, and to implement measures to mitigate these risks. This can help organizations to improve their overall risk management practices and ensure that they are prepared to respond to potential threats and vulnerabilities.
How to Achieve NERC CIP Compliance:
1. Ensure that network device configuration files are backed-up and versioned
One of the key building blocks of a network compliance program is the ability to go back in time and understand precisely how firewalls, routers, and switches have been configured and modified. This means setting up a backup system to keep a copy of network device configuration files at least once a day. It also requires defining file storage and data retention policy to organize and timestamp every configuration version for at least a year. An efficient backup system will enable compliance analysts to search and retrieve records when preparing for an audit.
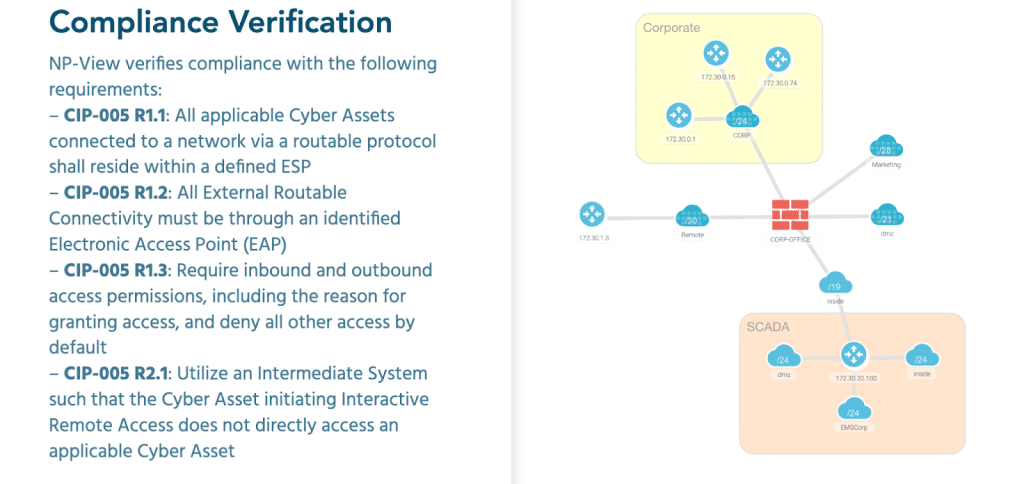
2. Verify that network topology diagrams and asset categorizations are up-to-date
We cannot protect what we do not know, and accurate knowledge about an organization’s network starts with a complete asset inventory. Once the inventory has been created, a process should be put in place to update it periodically. This also applies to the network topology diagram, which should clearly indicate where critical equipment is located and how networks are segmented into different access zones. A network map is crucial to enabling the compliance team to gain the same clear understanding of configurations to work efficiently with the security and networking teams.
3. Build baseline access policies that include rule justifications
Many organizations have a process to add new firewall rules, but they lack an efficient process to remove them. As a result, rulesets become bloated after a few years, and nobody dares to clean up old rules for fear of breaking something. The solution is for the compliance team to define baseline access policies that correctly implement internal controls and respect regulatory requirements. This way, network engineers have a reference to use when evaluating changes, and compliance teams can easily check for deviations from the baseline. It is also important to include rule justification directly in the baseline record so one can understand the business reasons for specific accesses.
4. Monitor baseline changes over time
Once baselines have been defined, a process should be implemented to monitor changes continuously or at least periodically. It is recommended that compliance teams use a system that is independent of the IT change management process to verify changes externally. Our advice is to leverage read-only configuration monitoring solutions that compliance analysts can easily use without having to add to the workload of the IT and networking team.
5. Track progress toward cyber resiliency
Finally, compliance teams should support the goal of their organization to become cyber resilient. This means gaining the ability to recover from and adjust rapidly to cyber risks. In practice, once a compliance framework has been established, the compliance team should organize periodic meetings with other stakeholders to review progress toward implementing resiliency techniques and to ensure everyone remains aligned.
Maintaining NERC CIP compliance requires a proactive approach to security and risk management and ongoing effort to ensure that your organization meets regulatory requirements.
– Reach out to one of our OT/ICS Specialists and hear more on the importance of micro segmentation –
Network Perception
Securing the Connected World