How to Build a Robust Risk-Based Compliance Framework

During the past 15 years, most energy organizations have built the culture and tools to handle effective year-round compliance verification.
Here’s how to develop a heightened risk focus into the picture. In the energy sphere, leaders should start by reviewing its respective regulatory resources made available by NERC, the Federal Energy Regulatory Commission (FERC), and relevant organizations like the National Institute of Standards and Technology (NIST). Once a compliance framework is established around those regulatory relationships, leaders should identify a dedicated compliance task force with clear roles and assignments close to key parts of the company infrastructure. That team should work within an independent process with a clear separation of duties.
Organizations can better protect their mission-critical assets by leveraging the critical infrastructure protection (CIP) requirements from the NERC compliance framework. The requirements specifically tied to network segmentation include:
- CIP-002 R1: Identify each of the medium and high-impact bulk electric system cyber assets
- CIP-005 R1.1: All applicable Cyber Assets connected to a network via a routable protocol shall reside within a defined ESP
- CIP-005 R1.2: All External Routable Connectivity must be through an identified Electronic Access Point (EAP)
- CIP-005 R1.3: Require inbound and outbound access permissions, including the reason for granting access, and deny all other access by default
- CIP-005 R2.1: Utilize an Intermediate System such that the Cyber Asset initiating Interactive Remote Access does not directly access an applicable Cyber Asset
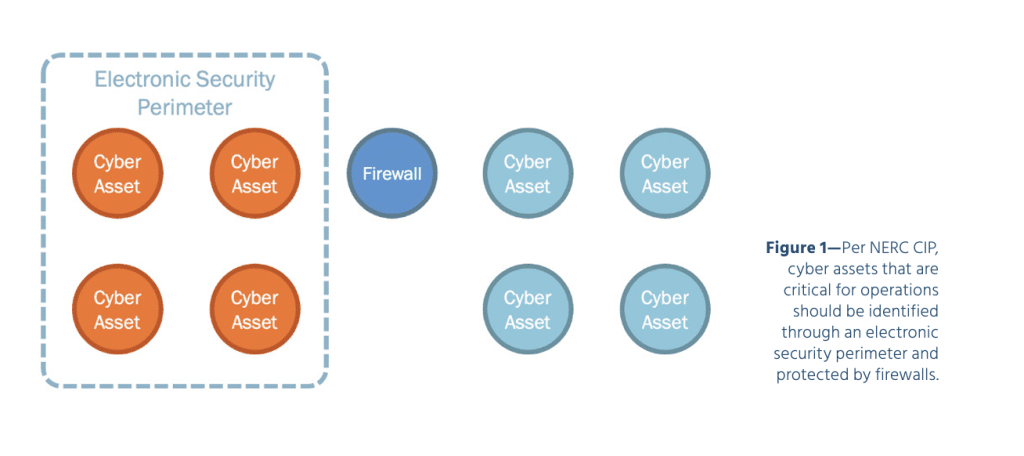
- CIP-005 R2.2: Interactive Remote Access sessions must be encrypted to the Intermediate System to protect the confidentiality and integrity of the communications (Figure 1)
Step-by-Step Independent Network Risk Verification Process
Organizations don’t need a size requirement to develop an effective risk-based compliance verification process. Most companies can begin with these three steps:
Step 1: Collect Access Policy Documentation
- Collect network access policy requirements based on the risk assessment framework
- Review existing documentation for network topology and asset inventory
- Identify connected critical assets: which applications require network access and why
Step 2: Establish Your Baseline
- Collect network device configurations, including firewalls, routers, and layer-3 switches (Figure 2)
- If possible, identify connected assets using the address resolution protocol (ARP) tables of your network switches
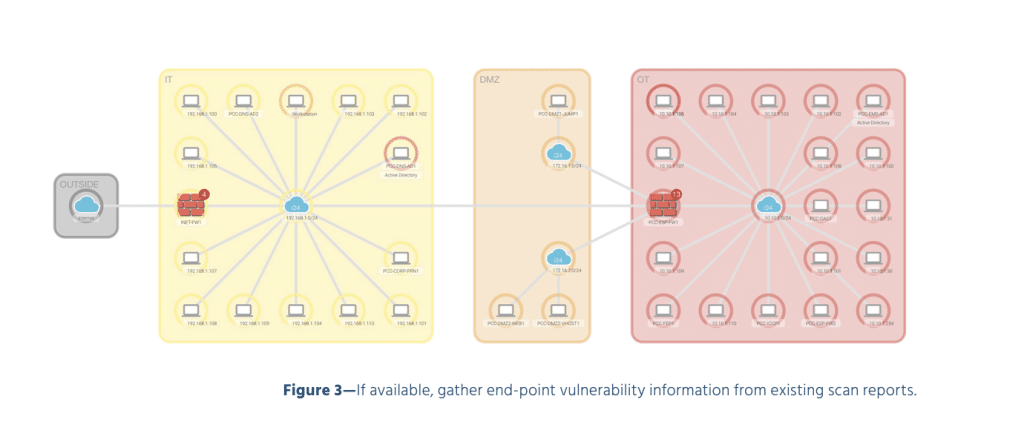
- If available, gather end-point vulnerability information from existing scan reports (Figure 3)
- Generate your network topology diagram and add network zone information
- Identify your respective “crown jewels” that need protection — such as critical cyber assets and their locations (this is the Electronic Security Perimeter (ESP) in the case of NERC CIP)
Step 3: Compare Your Policy Against Your Baseline and Document the Gaps
- Verify that access rules allowing inbound and outbound connectivity to and from the zones hosting your crown jewels match authorized communications
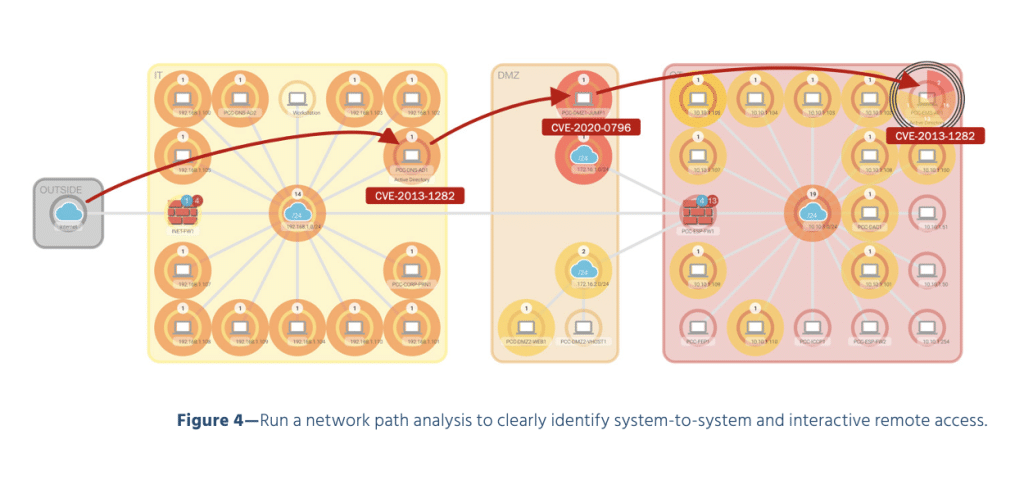
- Run a network path analysis to clearly identify system-to-system and interactive remote access (Figure 4)
- Document overly permissive rules, misconfigurations, and incorrect network segmentation (Figure 5)
Only resilient organizations can defend against sophisticated cyberattacks. Remember these steps in creating and conducting an efficient risk-based compliance verification process.
Watch our latest video demonstrating how NP-View can help you build a robust risk-based compliance framework or contact an OT/ICS specialist.