How Network Segmentation Helps Utilities Prevent Cyber Attacks
In a recent post about the 2 Sides of Network Visibility, we explored the importance of establishing cyber resiliency for all electric utilities, water, gas / oil / petroleum, and other critical infrastructure systems for both OT and IT network architectures to prevent disruptions.
These complex ecosystems are growing daily and, if not understood from all access points, are left vulnerable to persistent access. Operators need an effective strategy to respond to critical emergencies faster, including ways to understand, isolate, contain and mitigate threats.
How to Prepare for a Cyber Attack
Utilities today need:
- The right topology to visualize their networks
- The right network access policies
- Investment in environments with the right segmentation
With critical dependencies on connected cyber systems, industrial control systems need cyber resiliency to protect their mission-critical assets.
It requires an understanding of dependencies among cyber systems and critical operations:
- Which cyber systems the critical operations depend on
- How are those systems connected, and how are communications controlled
- How to increase resiliency moving forward
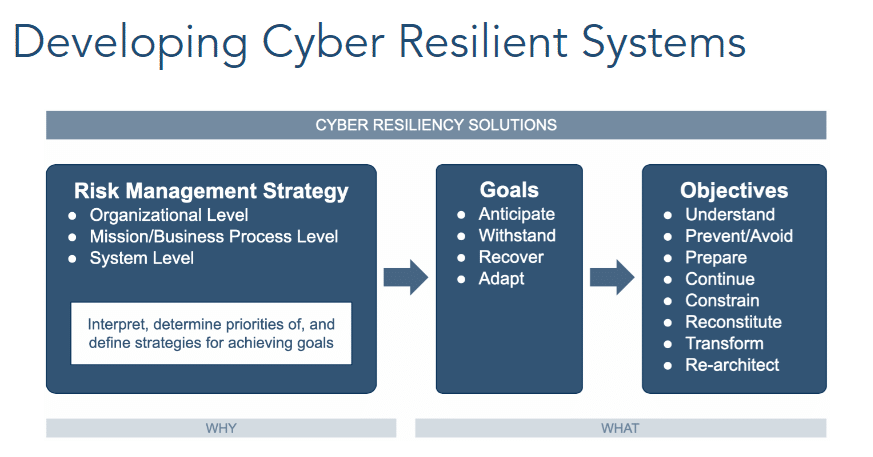
The foundation for creating cyber resiliency is a risk management strategy that includes Network Traffic Monitoring and Network Access Modeling.
Complementary Approaches to Cyber Resiliency…
Where to start?
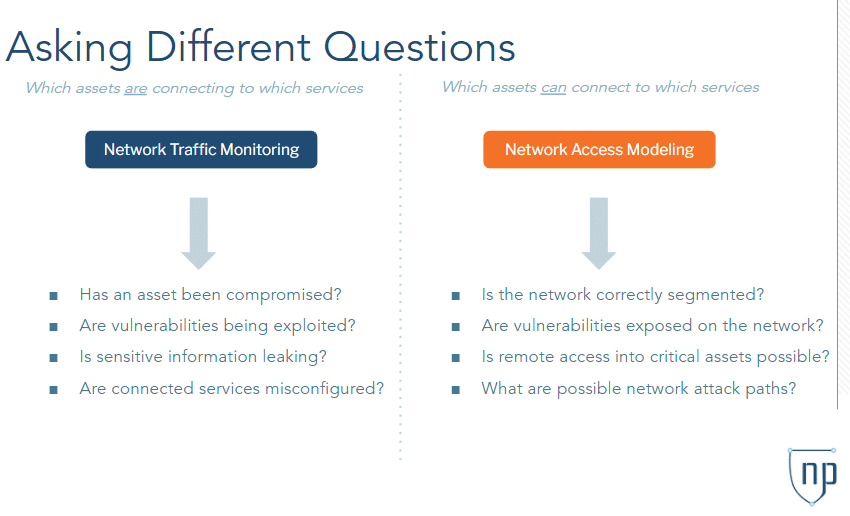
Each approach enables answering a different set of questions. On the one hand, network traffic monitoring is extremely useful for identifying compromised assets and exploited vulnerabilities. It’s also helpful to detect whether sensitive information is being exfiltrated or a connected service is misconfigured.
On the other hand, network access modeling enables the proactive verification of network segmentation, as well as understanding if critical vulnerabilities are exposed on the network. It’s also vital to measure risks related to remote access and to simulate possible network attack paths.
There is no doubt that to become cyber resilient, organizations must invest in both techniques, so they eliminate all blind spots through a comprehensive network visibility program.
An important question remains: where to start?
The answer depends on the resources available and time:
- Instrumenting a network to collect live traffic data typically requires multiple months of deployment.
- Collecting configuration files to build a network model usually takes only a few days.
Thus, we recommend starting with modeling to gain a fast and accurate understanding of your network architecture. This knowledge will then help plan for the deployment of sensors to augment your network visibility with live data.
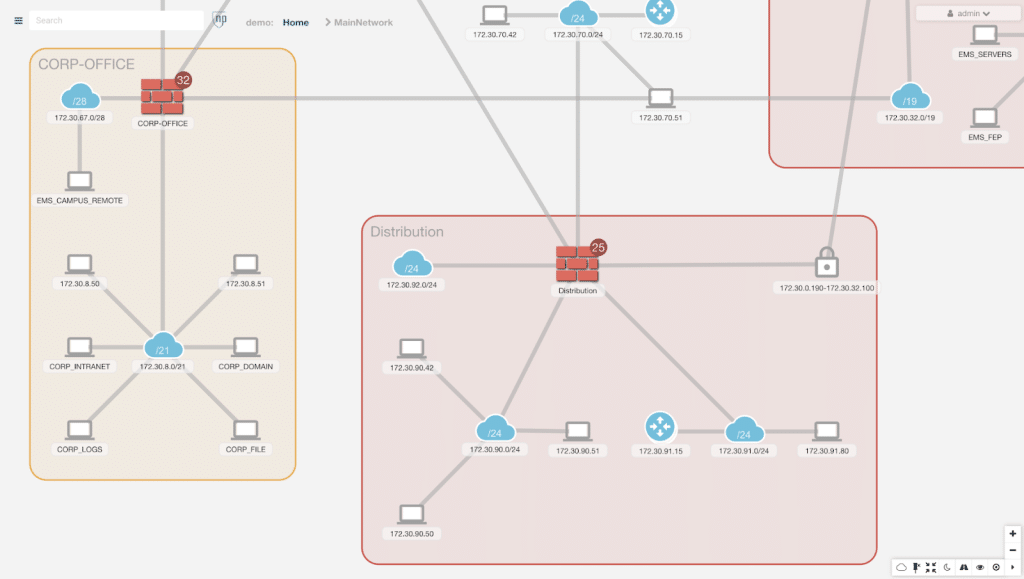
Principle of Least Privilege (Network Segmentation)
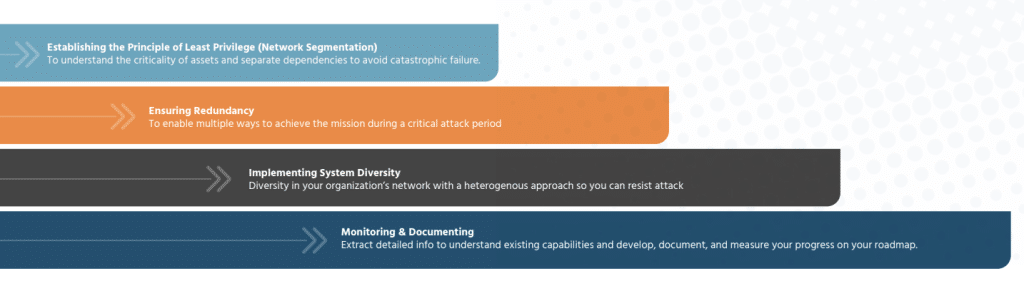
By leveraging the Principle of Least Privilege, or Network Segmentation, utilities can achieve a faster time to value and protection over longer traffic analysis solutions. Network Segmentation enables organizations to understand the criticality of assets and to separate dependencies to avoid catastrophic failure.
Segmenting a network is the most efficient way to prevent attackers from extending their reach through lateral movement. Unfortunately, network segmentation is easier said than done. Complex network environments going through frequent changes are prone to become more porous over time.
Network Perception recommends adopting a 3-step network access policy hardening approach:
- deny all access by default
- define network zones
- enable connectivity among zones on a strict need-to-know basis
If starting from a clean slate is not possible, then one should at least verify rulesets to identify overly permissive rules (e.g., “any” source or “any” destination) and reduce their scope.
Cyber risk alerts should be designed through collaboration with cybersecurity experts to ensure that any misconfigurations and cyber vulnerabilities are instantly identified. Each time a change in the network is detected, the cyber risk analysis checkers are automatically running over the modified configuration files to report possible issues.
With Network Segmentation in place, ongoing network risk assessments should include:
- Assessing the correctness of network segmentation
- Identifying risky network connectivity paths and misconfigurations in configuration files
- Understanding exposure of vulnerable assets
- Detecting overly permissive rules
- Reporting unsecured network protocols
- Cleaning up unused rules and object groups
- Importing security advisories to check for vulnerabilities
Cyber resiliency starts with understanding the entire OT / IT network so we can protect and make it as difficult as possible for an attack to take place. Then, make sure you can still operate when attacked, respond, and, most importantly – recover.
At Network Perception, our goal is to provide practical advice to:
- Security teams can adopt key techniques to build cyber resilience over time,
- Compliance teams can assess and track progress to help guide their organizations, and
- The utility industry can better understand the importance of and how to build visibility for a more cyber-resilient organization.
Using industry best practices, Network Perception automatically identifies potential risks related to network configurations. Using the Network Perception Connectivity Path analysis, the user can review each of the highlighted risks and make a judgment on action.
Read more about The 2 Sides of Network Visibility in our Complimentary eBook:
About Network Perception & NP-View
NP-View is a software product developed by a team of networking and security experts at Network Perception. It works offline and generates a network topology diagram by analyzing configuration files from firewalls, routers, and switches. The interface design of NP-View allows users to easily identify and track overly-permissive network access policies, as well as recording justifications for rules, ports, and services. If you have questions or would like to know more about NP-View, please contact the Network Perception team at:
+1 (872) 245-4100 | info@network-perception.com | Network Perception