Preparing for Cyber Attacks on Utilities, Gas / Oil, and Water: 2 Sides of Network Visibility
Preparing for Cyber Attacks on Utilities, Gas / Oil, and Water:
2 Sides of Network Visibility
In the past 20 years, our state, national, and local utilities have matured, and remote connectivity has only increased opportunities for disruptions, creating power outages and disruptions to electric, water, gas/oil, and other critical infrastructure.
As a result, companies are investing in cyber security solutions to keep the latest malware outside of their infrastructure. As shown by the recent Solarwinds breach, cyber security monitoring solutions can become an attack vector. As experienced by the 18,000 customers affected, cleaning up after the breach is highly stressful.
The goal of eliminating all cyber threats is futile since organizations will continue to depend on cyber systems, and attackers will keep targeting them. To succeed in overcoming this arms race requires investing in cyber resiliency. This means the ability to recover from and adjust rapidly to cyber risks. Like the immune system that has developed protection, detection, and evolution capabilities over hundreds of thousands of generations to keep organisms alive despite the constant assault from viruses and diseases, organizations have to embrace the principles of cyber resiliency to keep operating despite cyber threats.
These cybersecurity threats are rapidly increasing in both scope and severity. Keeping your critical infrastructure completely secure is unrealistic; being proactive & ready to assess, respond and recover is not.
New Cybersecurity Regulations Introduced
The US government is pushing new cybersecurity regulations to improve reporting and transparency surrounding cyber attacks.
- In March 2022, the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA) was signed into law and requires critical infrastructure companies to report covered cyber incidents and ransomware payments to the Cybersecurity and Infrastructure Security Agency (CISA).
- That same month, the Securities and Exchange Commission (SEC) proposed a rule requiring publicly listed companies to report material cybersecurity incidents to the SEC in addition to periodically reporting about organizations’ policies and procedures to identify and manage cybersecurity risks.
The new requirements offer a strong opportunity for companies to not only review and update their cybersecurity incident response plan but also to proactively invest in cyber resiliency principles, such as continuous visibility and verification of their network access policies.
Preparedness and the ability to understand the impact of a breach in a timely manner will be key foundations to comply with the new reporting requirements and to keep operating despite being under threat.
Cybersecurity requires a robust compliance program, redundancy to ensure business continuity, and diversity of tools. For this to work harmoniously, teams across many departments are imperative.
While cybersecurity is becoming more complex, simplicity and usability still matter. Balancing them with visibility, resiliency, and compliance is the goal of any cybersecurity framework.
The Solution: Establishing Comprehensive IT / OT Network Visibility
The first objective of cyber resiliency is visibility and understanding. It is defined in the NIST publication, NIST,SP.800-160v2r1 as maintaining useful representations of mission and business dependencies and the status of resources with respect to possible adversity.
These complex ecosystems are growing every day and, if not understood from all access points, are left vulnerable to persistent access. To respond to critical emergencies faster, companies need to put in place the right incident response capabilities, so we can understand, isolate, contain, and mitigate threats when they occur.
Utilities today need:
- the right topology to visualize their networks
- the right network access policies
- the right segmentation
With critical dependencies on connected cyber systems, industrial control systems need cyber resiliency to protect their mission-critical assets.
It requires an understanding of dependencies among cyber systems and critical operations:
- Which cyber systems the critical operations depend on
- How are those systems connected, and how are communications controlled
- How to increase resiliency moving forward
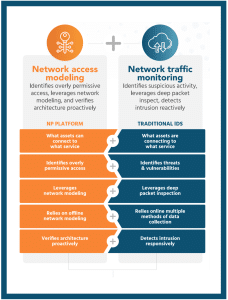
Gaining accurate visibility of OT networks is fundamental to protecting critical assets and ensuring that networks are correctly segmented. A comprehensive network visibility solution combines traffic monitoring (what is connecting to what) with network architecture analysis (what can connect to what).
The 2 Sides of Network Visibility: The First Step Towards Cyber Resiliency
Network visibility is covered by the following two building blocks under visibility & understanding. These two sides of network visibility are both crucial and complementary to each other:
- Analytic Monitoring: Monitor and detect adverse actions and conditions in a timely and actionable manner. Analytic monitoring means understanding which assets are connecting to which services right now. It’s a reactive technique that relies on network instrumentation such as TAP or SPAN to collect live traffic and dissect protocols through deep packet inspection. It provides visibility on all active endpoints that communicate through network paths on which a sensor has been deployed.
- Dynamic Representation: Keep the representation of the network current. Enhance understanding of dependencies Dynamic representation, or network modeling, means understanding which assets can connect to which services. It’s a proactive technique that relies on configuration files from firewalls, routers, and layer-3 switches to model the network topology and analyze connectivity paths. It provides accurate visibility of the network architecture and enables risk assessment without having to deploy a sensor or agent in the environment.
Want to learn more? Download our Guide https://network-perception.com/resource/ebook-invest-in-2-sides-of-network-visibility
Complementary Approaches:
Each approach enables answering a different set of questions. On the one hand, network traffic monitoring is extremely useful for identifying compromised assets and exploited vulnerabilities. It’s also useful to detect if sensitive information is being exfiltrated or if a connected service is misconfigured.
On the other hand, network access modeling enables the proactive verification of network segmentation, as well as understanding if critical vulnerabilities are exposed on the network. It’s also important to measure risks related to remote access and to simulate possible network attack paths.
There is no doubt that to become cyber resilient, organizations have to invest in both techniques so they eliminate all blind spots through a comprehensive network visibility program.
Once you understand and visualize what is on your network map and how this might be changing every day – then you can apply additional cyber resiliency principles to develop your cyber resiliency roadmap like:
1) Establishing the Principle of Least Privilege (Network Segmentation)
To understand the criticality of assets and separate dependencies to avoid catastrophic failure.
2) Ensuring Redundancy
To enable multiple ways to achieve the mission during a critical attack period
3) Implementing System Diversity
Diversity in your organization’s network with a heterogenous approach so you can resist attack
4) Monitoring & Documenting
Extract detailed info to understand existing capabilities and develop, document, and measure your progress on your roadmap.
Our dependence on cyber systems is increasing every day, and the frequency, severity, and sophistication of cyber-attacks have been rising along with it. The size and complexity of networks have also grown exponentially, continuously exposing organizations to larger attack surfaces. As a result, companies are investing in cyber security solutions to keep the latest malware outside of their infrastructure.
Cyber resiliency starts with understanding the entire OT / IT network so we can protect and make it as difficult as possible for an attack to take place. Then, make sure you can still operate when attacked, respond, and, most importantly – recover.
It’s never too early – or too late, to protect our vulnerable utilities and infrastructure systems. Contact us [LINK] and let us help you with your cyber resiliency strategy.
Watch this short video of our product and see what you can do to become cyber resilient.
If you have questions or would like to know more about NP-View, please contact the Network Perception team at:
+1 (872) 245-4100 | info@network-perception.com | https://www.network-perception.com